Cohesity's innovative DataProtect technology is based on a powerful and flexible hyper-convergent architecture that can protect physical and virtual platforms, databases and applications, in a single cutting-edge application-oriented solution which extends from on-premise infrastructure to the cloud
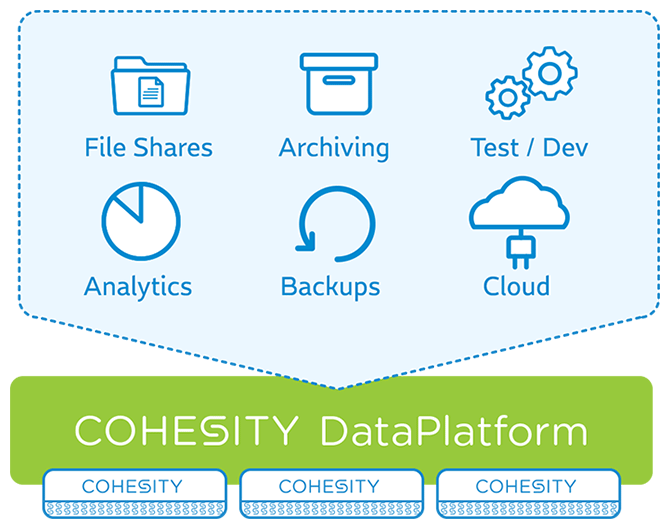
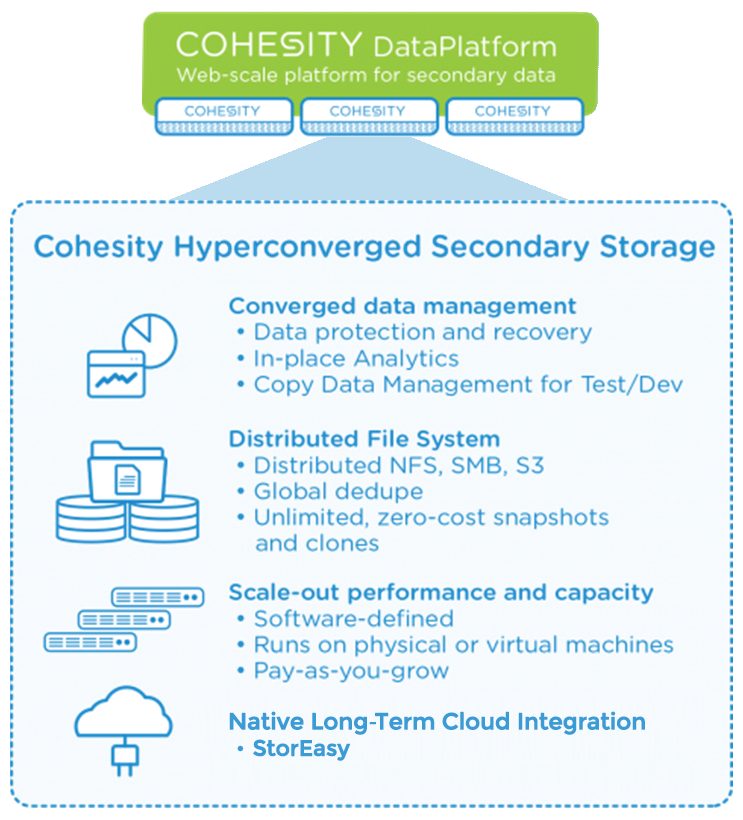
Cohesity has developed an innovative architecture to consolidate traditional storage silos such as backup software, data deduplication, file storage and cloud gateway into a single scale-out platform to create an easy to manage, efficient and scalable environment.
Unlike other solutions which use backups as a primary resource, the DataProtect technology is able to create clones of any type of data (backups, files, objects) on a huge scale, at any moment, without impacting performance. The data is presented in NFS / SMB / S3 with no restrictions and high-performance allowing applications to use the data transparently without changing the way they work.
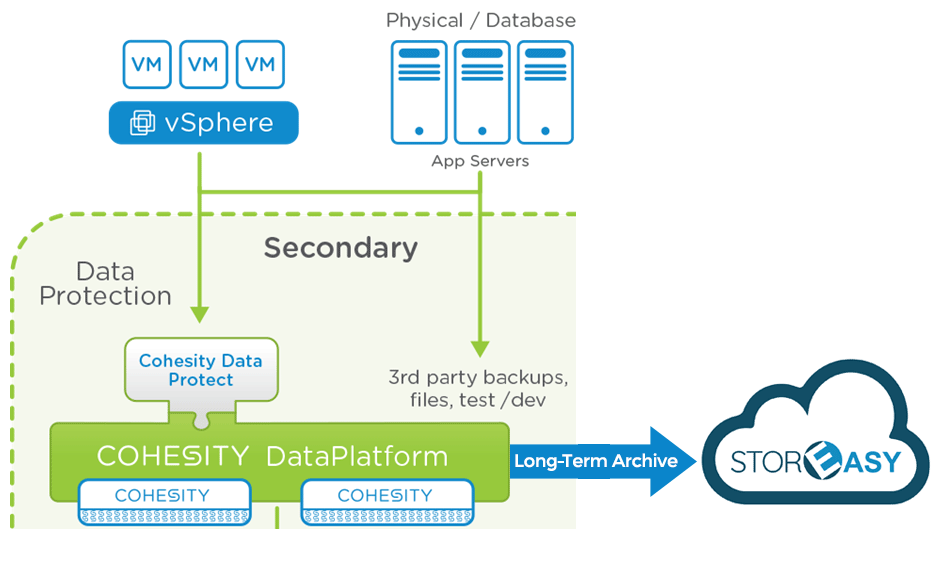
StorEasy is the first Cloud Storage Provider that can guarantee native integration with the DataProtect solution to deliver Long-Term Archive services through an active archive platform certified by Cohesity
To manage long-term archiving for the innovative platform Cohesity DataProtect, StorEasy developed a sophisticated active archive architecture based on LTO tape technology.
The purpose of an active archive environment is to render all content online or near-online (in the case of of tape libraries) using extremely reliable and long lasting storage technologies. The hybrid architecture uses different storage tiers to ensure high performance and low operating costs compared with traditional disk-based storage systems.
Tape, and in particular LTO technology, is not only economical for a second or third security copy, but also offers extraordinary reliability with an error rate 10,000 times lower than a SATA disk and guaranteed data legibility on LTO media for a period of 30 years.
The active archive solution includes data caching at the writing and reading stages. In practice, a portion of the archived data remains as a twin copy on the cache. How long the data stays in the cache is determined by policies which allow you to decide dynamically what and how much data to keep.
This enables you to read the data immediately without having to access the tapes in the tape libraries. Naturally the cache must be suitably sized to keep online only the data that has to be accessed for some reason within a certain period of time. The duration of the data on the cache disks and the thresholds can be programmed dynamically. Should these be exceeded, the cache is emptied of the least accessed files (obviously all data is already archived on tape independently of what occurs in the cache).
Long-term archiving for Cohesity DataProtect
LTO/LTFS tape technology
LTO tapes provide a secure, reliable and economic technology that can store information for a period of up to decades, an elastic memory that can be used to store unlimited quantities of data extremely securely at a fraction of the cost of any other storage technology available on the market today. LTO tapes offer an error rate 10,000 times lower than a SATA disk and guaranteed data legibility for a period of 30 years, support a million recordings and 20,000 writing cycles per tape, with an MTBF (Mean Time Between Failures) of 250,000 hours at a 100% duty cycle. Not to mention that a single LTO-8 tape offers a native capacity of 12 TB and 30 TB compressed.Linear Tape File System (LTFS)
The increased popularity of tape-based active archive architectures is largely due to the diffusion of the ISO/IEC 20919:2016 compliant Linear Tape File System (LTFS).
The most significant feature of the LTFS format is the ability to move recorded media between different operating systems, applications and platforms, allowing you to use the tape like a traditional hard disk (standard volume with directories and subdirectories).
General Data Protection Regulation (GDPR)
 StorEasy’s Long-Term Archive protection is in line with the General Data Protection Regulation (GDPR) and all those applications and standards which require secure archiving for extremely long periods such as legal, accounting and administrative documents which must be archived by law for 10 years, and others for much longer periods, sometimes indefinitely.
StorEasy’s Long-Term Archive protection is in line with the General Data Protection Regulation (GDPR) and all those applications and standards which require secure archiving for extremely long periods such as legal, accounting and administrative documents which must be archived by law for 10 years, and others for much longer periods, sometimes indefinitely.
WORM Archiving (Write-Once Read-Many)
WORM technology can archive data in non-rewritable, non-erasable format. Using this technique, recorded data can no longer be overwritten, modified and/or manipulated. The WORM protection process offered by StorEasy for long-term archiving complies with the strictest national and international regulations covering sensitive data archiving, document management, electronic record storage and log file archiving. The solution guarantees secure and lasting validity of archived data that is binding on third parties thanks to full compliance with the requisites of law.
Data at Rest Encryption for data archived on LTO media
The Long-Term Archive Service uses the Advanced Encryption Standard (AES), one of the most popular and secure cryptography algorithms on the market. AES is impregnable to attack, and it is no accident that this is the standard chosen by governments, banks and high security systems worldwide. Cryptography ensures that the LTO tapes can only be read by those who possess the correct decryption key. The data is encrypted directly on the LTO tape units, using the AES-256 key, by specialized hardware in the tape library drives.
Secure Hash Algorithm (SHA) for data integrity control
In addition to the manufacturers’ guarantee of the integrity of data recorded on tape for long periods of time, StorEasy has introduced further levels of integrity control for data recorded on LTO tapes.
To ensure that the archive is readable in the event of damage, wear and tear or corruption of the magnetic support, scheduled scans of the LTO media in the tape libraries are made to read the checksums introduced during the writing of each file.
The data integrity check is achieved via the hash function, an algorithm which, for an arbitrary quantity of input data, generates an output of a fixed size as a “fingerprint” of the incoming data. This operation is repeated for each archived file, and the hash created by the Secure Hash Algorithm (SHA) is stored together with the file. The hashes are recalculated and compared during the scans to check the integrity of the media. If a hash is found to be incorrect during validation, the associated file is marked “bad” and another copy of the file (offline security copy) is retrieved in real time to replace the corrupted one and restore the correct number of copies. Then a second (or third copy) of the file is made on a new media.

